Internet Message Access Protocol (IMAP) allows remote manipulation of messages on the server. IMAP was implemented in response to the shortcomings of POP; including an inability for sophisticated mail manipulation on the server, and restricted access to mail from more than one computer.
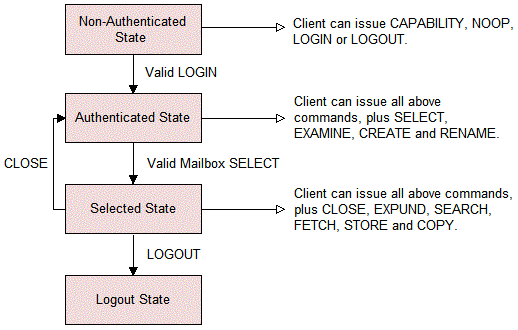
Similarly to POP and other protocols, the IMAP server responds to commands issued by the client. Every command is preceded by a unique, client-defined identifier (for example, A0001), which increments with each successive command. These commands allow a client to create and manipulate folders called "mailboxes" on the server in a way that is functionally equivalent to manipulating local folders. As commands are issued, an IMAP4 session progresses through four states: non-authenticated, authenticated, selected and logout.
IMAP4 Non-Authenticated State
When a client makes a TCP connection with the server (typically on port 143), the session enters the non-authenticated state. In this state, the client has access to four commands: CAPABILITY (displays special capabilities of the server), NOOP (causes the server to give a positive response), LOGIN (authenticates the client), and LOGOUT (ends the session). In order for the session to continue, the client must supply authentication credentials with the LOGIN command. Once proper credentials have been supplied, the session moves into the authenticated state.
IMAP4 Authenticated State
In the authenticated state, the client has access to all commands from the non-authenticated state (except for LOGIN). The client can also CREATE a mailbox, get the STATUS of a mailbox, RENAME a mailbox, and perform other commands involving the manipulation of mailboxes. The client may also select a valid mailbox using either the SELECT or the EXAMINE command, followed by a valid mailbox name. SELECT opens the mailbox with read/write privileges, whereas EXAMINE opens the mailbox with read-only privileges. Once one of these commands is executed successfully, the session moves into the selected state.
IMAP4 Selected State
Messages are accessed in the selected state. The client can issue any of the commands from the authenticated state, as well as CLOSE (closes the mailbox and returns to authenticated state), EXPUNGE (removes all messages flagged for deletion), SEARCH (allows the client to find messages using certain criteria), FETCH (returns all or a part of a message), STORE (allows updating of flags stored with each message), and COPY (allows a message set to be copied to a mailbox). From the selected state, the client may use CLOSE to return to the authenticated state, or LOGOUT to go to the logout state.
IMAP4 Logout State
In the logout state, the server simply terminates the connection.
The graphic below illustrates this progression through the four states.
IMAP4 Sample Dialog
The following demonstrates a typical dialog between a client downloading messages from a server using the IMAP protocol.
< connection > Client: A0001 LOGIN username password Server: A0001 OK LOGIN completed Client: A0002 CREATE mailbox1 Server: A0002 OK CREATE completed Client: A0003 SELECT mailbox1 Server: A0003 OK SELECT completed < note: since this is a newly created mailbox, no mail exists > Client: A0004 FETCH 1:3 Server: A0004 BAD FETCH Client: A0005 Quit Server: A0005 OK QUIT completed < connection closed >